
KRACKing the WPA2
A couple of days ago we got news that a security flaw was discovered in WiFi Protected Access II (WPA2). Considering that WPA2 is around 14 years old, it’s a wonder that the flaw hadn’t been found earlier. The attack is called KRACK (Key Reinstallation Attack) and uses a Man in the Middle (MitM) attack methodology. It happens during the 4-way handshake phase and revolves around client using an all-zero key to encrypt communication with an Access Point (AP).
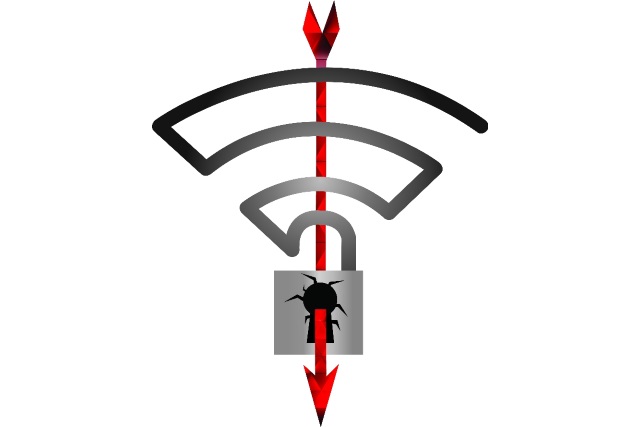
How does it work?
Most of the news spin around the title CRACKED, even though the vulnerability isn’t in the protocol itself, but in its implementation. WPA2 protocol is mathematically proven to be secure, it describes how parties should establish a secure connection, but not when. KRACK exploits this by intercepting responses at a particular point in time resulting in a predictable behavior from both parties.There are couple of requirements which need to be met in order for the attack to work.
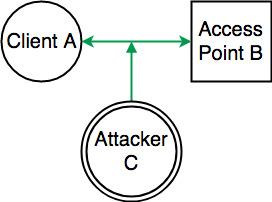
Rogue channel
C needs to create an AP rogue channel in order to sniff data packets in A -> B communication. This way C impersonates B only on a different broadcasting channel. C can see data packets being transmitted, although they will be encrypted. The danger here is that C doesn’t need to be connected to any network at all, so he doesn’t need to know B’s password.4-way handshake
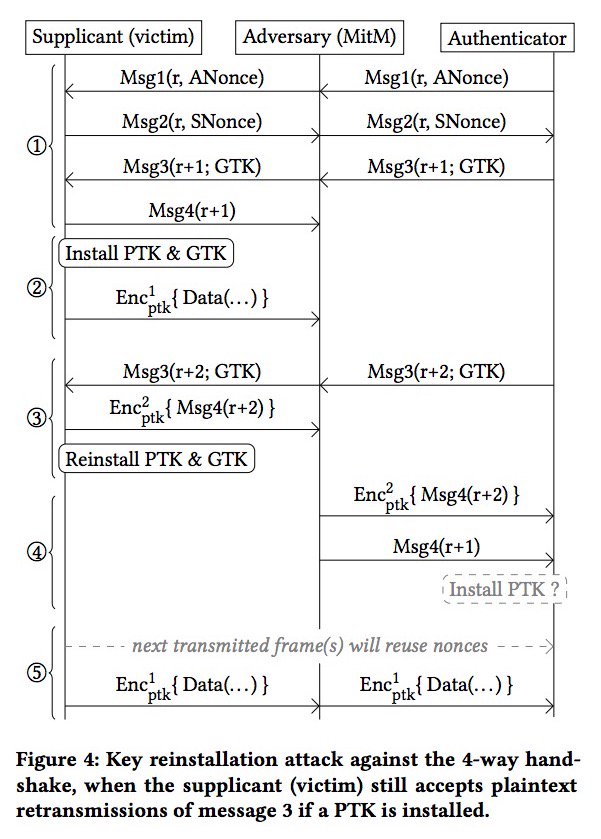
In order to establish a connection, A and B need to perform a 4 way handshake. This means that the initial communication will consist of 4 messages between A and B through which they will prove to each other that both know the Pairwise Master Key (PMK) generated out of the network’s (B’s) passphrase without even disclosing the key. This assures that rogue AP channels (above) won’t be able to decrypt data.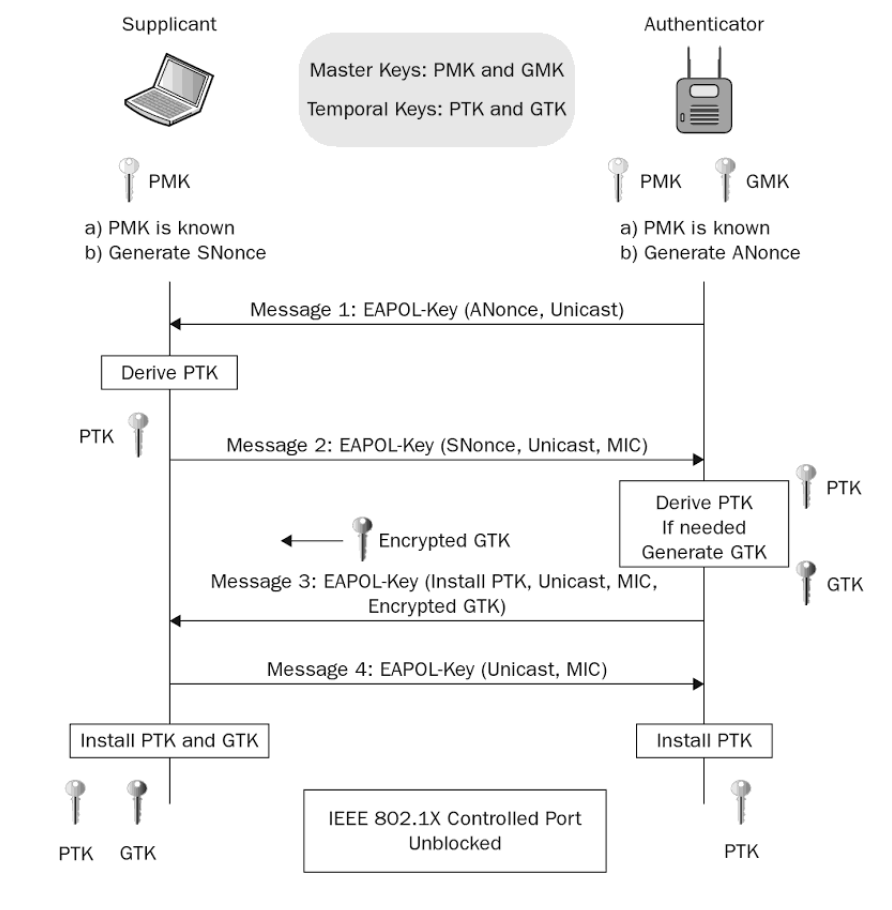
The first 2 communication steps revolve around assuring that the PMK is known from both parties. B will encrypt a message with PMK and forward encrypted message with its current nonce to A. A will decrypt the message with its PMK, increment its nonce, encrypt message again and send response to B. If this communication is consistent they jump into critical step 3 where KRACK is possible.
At step 3, B will generate a Pairwise Transient Key (PTK) out of:
- PMK
- A nonce and MAC address
- B nonce and MAC address
But what happens if B nevers gets A’s response about the installed key? B will resend the PTK to A which will repeat the key installment and nonce increment process. This will result in A resetting its nonce and replay counter and install the already used PTK. At that point we can stop interrupting A’s response, which B will confirm and the handshake is ended.
In each of the communication steps they send each other incremental nonces (number to be used only once). By combining current nonce with the key, they are able to generate a series of 0s and 1s which is called a keystream. By XOR-ing keystream and plaintext data ciphers encrypt messages.
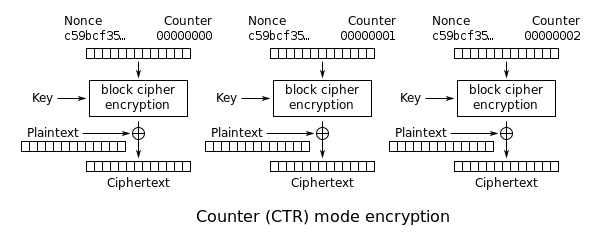
The KRACK exploit not only enables us to decrypt the traffic, but depending on the initial setup it can lead to forging and even injecting data frames sent to the client.
Official video presentation showcases use of a rogue AP channel, running a KRACK attack with all-zero key installation, SSL strip method and displaying the plaintext data.
Sources:
- Official website disclosing the vulnerability - https://www.krackattacks.com
- Detailed mechanism https://papers.mathyvanhoef.com/ccs2017.pdf
- Current patch status https://char.gd/blog/2017/wifi-has-been-broken-heres-the-companies-that-have-already-fixed-it

